
Zero to Zen: Instant, Easy Wins for Your Online Life
Tips and tricks for a totally zen online life, in terms of privacy, security, and cleanliness.
If you are anything like me, you trial all kinds of new digital products, creating accounts here and there, and you probably keep a few email addresses around—or you have an overburdened, overtaxed poor Gmail/Yahoo/Hotmail account that has suffered, but worked, faithfully through the years. It’s easy to get into a sticky situation, with a mess all over the place. And your computer! Man, you don’t even want to think about that poor sod… 🧟♂️
I was recently doing a bit of check-up on my online accounts and presence as I tend to do every year or so and thought it might be worthwhile to share some of my own tips, tricks, and philosophy around computer zen, since I know from experience that, to be honest, most people are a lot less of a structural fetishist than I am. I’m sure there will be a few nuggets here for most of you who want to reach the zen of online life!
We’ll go through three major areas—security, integrity, and cleanliness—with a number of proposed tasks for each.
Tighten your security posture
Updates, unloved but important
⏲️ ~5 minutes
Update your browser(s), software, and your computer. I think it’s well worth turning automatic updates on pretty much everywhere, and it’s not harder than flicking a switch.
Here’s how to do it:
Most things that aren’t Microsoft-made (sorry not sorry) won’t drop a Teams call to haphazardly update anything, but will actually ask politely.
Not updating your s**t is a real security hazard, so be a grown-up! And you know what? It feels good too 🏖️!
Use backups
⏲️ ~10 minutes to do basic setup + upload time for syncing content
This item is so ubiquitous for some of us that I even forgot to mention it in the first version of this article!
Not having any backup solution is a major problem. The desired state should be that you could theoretically throw your devices in an incinerator at any point in time and still know all (or the vast majority) of data is still intact.
If you are on a smartphone, chances are you have some sort of automatic backup of its data already, such as Apple’s iCloud.
I’ve used several solutions over the last 20 years, including:
- Dedicated internal hard drives (internal)
- External hard drives
- Large-size memory drives
- Dropbox, Google Drive, and similar desktop solutions
- Hosted Git (GitHub, GitLab…)
- iCloud
- Cloud storage
My tip here is to choose something that fits the type, quantity, and frequency of backups you need. In my case I use a paid iCloud plan (~$1/month) for my Apple devices to keep the phone and laptops continuously synced, and then Proton Drive for large, infrequent backups. Both of these options are reasonably priced, easy to use, and work very well. There are many options, so take the time to read the provided article if you need more grounding.
Backups are boring, but they'll save your bacon. Here's how to make sure your data lives on, even when your PC doesn't…www.wired.com
Are you leaking?
⏲️ ~5 minutes
Did you know that you can easily check if your passwords and credentials are leaked? If not, then you probably want to do this now.
There are online sources like Have I Been Pwned? where you can check if your email address is connected to a leak, and if you the built-in password manager on an iPhone, you can see if you have weak or leaked passwords.
Below I’ll explain more about what you can do to secure your accounts, regardless of whether your credentials are being breached or not.
Crank up the password strength and use unique passwords
⏲️ Depends on the number of sites/apps, expect several hours
Wherever you use passwords (which is most places), consider long passwords. Some advocate passphrases—which are easy for you to memorize but hard for a computer to randomly break — while others (more classically) advocate the use of long random strings using exotic characters, letters, digits, and everything in between. Any way you want to cut it, use passwords that are “hard” and long if you don’t know which approach you like most.
It’s quite common in modern operating systems or browsers to provide support for “keychains” and automatic password generation and completion.
If you need an online resource for any reason, Norton provides a free password generator that lets you tweak the parameters and overall password strength.
Oh, and never ever reuse a password. That’s a really bad idea. Expect that any time there is a leak/breach/hack, all those passwords will go into hackers’ databases and they will try to reuse those passwords for other sites. Ergo, a leaked credential at site X will be used to attempt to get access to site Y.
Upgrade to multi-factor authentication or passkeys
⏲️ Depends on the number of sites/apps, expect 0.5–2 hours
Don’t trust a password-only solution!
While not a bulletproof solution, use a password manager to fill in and remember your passwords. Your device probably already has one, if you are on a more recent one.
If you want to extend your system-native password manager, I recommend Bitwarden, which is open source, has a good free plan, and has good reviews.
Whatever you do, avoid LastPass which has been hacked several times.
Old-style multi-factor authentication (MFA) like SMS messages or emails are better than (literally) nothing but I would strongly advise against them if there are other options, given that an adversary can relatively easily spoof those.
Wherever possible, just bite the bullet and add whatever additional security layer is available, whether it be MFA or passkeys—here’s some additional reading if you are using iPhone. MFA is typically available in software form (via authenticator apps like Google Authenticator or Authy) and hardware form (such as via Yubico hardware keys).
Depending on your level of paranoia and requirements, you’ll probably be fine with software MFA for most things. It’s really easy to use once you’ve tried it once, trust me. And the chances of getting your accounts hacked will be significantly smaller!
Nuke those browser extensions
⏲️ ~5 minutes
While there are some good browser extensions out there, act as if they are malware by default. Set a very high bar that they need to pass through to allow them on your system. Always read reviews and make an informed assessment on every extension you allow to run.
Each of us has probably installed some kind of browser extension at least once: an ad blocker, an online translator, a…www.kaspersky.com
Clean up third-party connections and integrations
⏲️ ~15–30 minutes
You’ve probably set up some “third-party” connections over the years, such as letting you use your Google account to log in to sites/apps such as Spotify, LinkedIn, or Medium. It’s not uncommon that bigger platforms offer this possibility so give your platform(s) of choice a look-see in this department.
For Google specifically, you can see the third-party accesses under “Third-party apps with account access” on your Security page. If you are a developer, you might also want to check all the approved third-party integrations in GitHub.
Delete any unwanted or unused ones laying around.
Check up on your integrity
Remove unused accounts
⏲️ Depends on the number of sites/apps, expect several hours to a full day

As an Apple device user, I can see all my passwords in the password manager in iPhone, or use Mac’s standard Keychain Access application to do the same. If you use an external tool to manage passwords, you can of course do the same, and I expect Windows and Android users to have something in the same vein.
You can use all these tools to get a glance of where you have accounts—though of course, only if you’ve saved the credentials! Given that you do, you now have an excellent opportunity to filter out all the “oh I forgot about that” and “wth, is that crap still there” moments.
While this is not fun, to say the least, taking the time to prune and delete accounts on sites or apps you’re not using may be a very smart move.
Think of all the data that’s just lying around; it may even be private, sensitive, or financial in nature, in which case I can only highly recommend you go for a cleaning day if you’ve never done so before.
Never forget: Don’t share credentials! If that site is actually hacked, you have nothing to fear as it’s just garbage anyway and there is no way to backwards-engineer the password for any other site.
Most apps and SaaS products include built-in functionality to remove your account and data, but for quite a few websites, this is not to case. I know I’ve had to search for “APP NAME how to delete account” more than once! You might need to directly request this from their customer support if such functionality is not provided.
For things that seem completely trivial or unlikely to contain anything of particular value, I’ll just delete the record of the credentials in the password manager: “Out of sight, out of mind”.
Get a privacy- and integrity-respecting browser
⏲️ ~5 minutes
While I am a European, and I greatly value the meaning of the GDPR and our overall privacy legislation, I’m in no way a privacy zealot. With that said, I am definitely biased towards using a browser that respects my privacy and which just happens to be snappy to use and that works brilliantly in my day-to-day life.
If you’re scouting for options, there are comparison lists like these from Proton and NordVPN you can refer to. Generally speaking:
- Chrome is to be avoided.
- Apple’s Safari browser is a pretty good choice.
- Firefox is the best “conventional” option, being well-lauded and well-supported.
- Some (at least superficially) even more privacy-leaning options include the niche browser Epic and Brave.
You can always tweak some of the settings to make a browser even more privacy- and integrity-respecting.
Migrating bookmarks etc. is typically very easy, so don’t fret about stuff like that too much.
I can’t really seem to wean myself off of Safari, to be honest, given it does a good job and is also so neatly integrated into the Apple ecosystem, but going to Firefox should be a perfectly fine option for most—I keep it as a backup browser when Safari acts up. And it’s a brilliant and super-fast browser, too!
Add a better DNS resolver
⏲️ ~5 minutes
Using a custom DNS (Domain Name System) resolver can assist you with better internet speeds and a more secure connection. While this might sound like technobabble and hard to get working, it’s actually surprisingly easy. One of the better and more common options is Cloudflare’s 1.1.1.1 app.
When the Internet was built, computers weren't mobile. They sat in offices next to data centers. The Internet has…1.1.1.1
They write:
Your Internet service provider can see every site and app you use — even if they’re encrypted. Some providers even sell this data, or use it to target you with ads.
1.1.1.1 with WARP prevents anyone from snooping on you by encrypting more of the traffic leaving your device.
We believe privacy is a right. We won’t sell your data, ever.
It works both on computers and smartphones/tablets and is overall an easy, good upgrade to add while you are at it.
Move to a good, paid email service
⏲️ ~30 minutes with configuration
I moved to Proton Mail a few years ago. Some of the reasons for that were:
- Practically always, if something is free, then “you are the product”—this is certainly the case with Google products.
- I could accept the above fact to some extent, but it’s just a constant barrage of ads in the Gmail app so I ran incredibly tired of using it.
- The other free options, like Zoho, are functional but outrageously bad and bloated.
- I’ve had a domain with my name for many years, and I want an email address with that domain.
- Gmail doesn’t have custom domain support, of course, so even if I don’t hate it per se, I needed another option.
If you are in the same boat and looking for options, I can highly recommend Proton Mail.
Proton provides easy-to-use encrypted email, calendar, file storage, and VPN built on the principle of your data, your…proton.me
Proton has a great reputation, great UX and mobile app, offers a base email domain (so you don’t need to own your own domain), offers true encrypted email support, it’s got all the features I need (and some more that I grew into), and a fair price. Also, they are strongly committed to being privacy-respecting. I was sold.
At the end of the day, you get a markedly better experience, a massive boost of privacy of communications, you don’t get your data and behavior sold, and it’s all for the price of a big coffee-to-go.
Get your cleanliness act together
Remove all non-critical notifications
⏲️ ~15 minutes
If there is one mental health trick you need to afford yourself, it’s this one—and it won’t cost you anything at all.
Science and sheer lived experience has taught us all that incessant pings and alarms on our devices disturb our attention and concentration, sleep, ability to enjoy our lives, and more. In short: They destroy our lives and happiness, and give nothing back in return.
I’ve had the vast majority of my notifications off for years now. The more important ones I allow a badge for, and only the most critical ones may also send a vibration and sound. Same goes for work—I set Slack to only inform me about mentions and direct messages, and only some emails get “special” treatment.
Overwhelmed by device notifications? Here's a step-by-step approach to decluttering alerts so you can focus on what…zapier.com
While there are certainly (small, easy) technical steps involved here, the real battle is shaping your own habits; I can recommend James Clear’s Atomic Habits if you want some ideas and support for doing so.
Get that filthy hardware cleaned
⏲️ ~5–30 minutes
While not an online activity, take a few minutes and clean your laptop/device, because if it’s anywhere near as grimy as my laptop gets, then your laptop (and mom) will thank you for it.
You don’t need anything expensive or special, but it might be worth getting a few multi-purpose microfiber cloths next time you go out shopping.
Like your bathroom or your car, it's a good idea to regularly clean your laptop, and it's not difficult to do. You may…www.theverge.com
Erasing is the best protection
⏲️ ~30 minutes to several hours
Back in the early 2000s, my friends and I took installing TinyXP and ruthlessly optimizing the performance of near-the-brink-of-death machines to an art form. We performed autoexec.bat and other process management wizardry like no one else. But to do our feats of magic, we had to go hard. Nothing was out of reach, everything was fair game. It always started with a clean slate — remove any trace from before. No dilly-dallying, no half-measures.
Modern computers do essentially the same things today that they did 20 years ago — but to be honest — today we are seemingly accepting worse programming and in effect, new computers are slogging with something our old machines did just fine.
Remember Ripley from Aliens?

While this is a decent, albeit extreme, solution to problems you do have, we can always strive to not get them at all:
“What you don’t got, ain’t your problem.”
In regard to my opening statement, you can conveniently extend this maxim to, for example, programs and processes on your computer. While a new computer “feels” great and snappy, one of the reasons it does so is simply because there isn’t a ton of junk running on it uncontrollably (well, unless you bought some Chinese cheapo brand that will be loaded with malware and bloatware). It’s slow because there’s a lot of stuff going on and probably doing so in a really inefficient manner. Without a lot of stuff, we don’t have to care if it’s hyper-optimized or not, because “what I don’t got, ain’t my problem”. That’s a good place to be in. So:
- Stop things from auto-starting when you boot up (Mac, Windows).
- Delete apps you don’t use.
- Remove unused files or archive them.
Trust your fan! On a laptop, you can probably even feel the actual, physical heat emanating from it. A quiet, cool laptop is a happy laptop.
You can always use the Activity Monitor (Mac) or Task Manager (Windows) to understand what’s drawing attention from your machine right now. It’s not uncommon for some rogue process or wonky Visual Studio Code extension to thrash your computer. Use these tools to better understand what’s actually going on if you get poor performance or responsivity (or a loud fan). See more in the article linked below .
Auto-starting apps can use up valuable memory space and processor time. You can control this by using tools and options…www.theverge.com
Manage those tabs
⏲️ ~15 minutes
We’ve come to accept that a single tab (Confluence, I’m looking at you!) can utterly crush a €2500 machine these days. The same concept applies to open tabs, which tend to run in the background, drawing power and memory.
More importantly, I see myself losing a ton of focus with a thousand things open all at once; I find it to be like coming to someone’s messy home. To these “messy people”, I can only recommend Cal Newport’s book Digital Minimalism: Choosing a Focused Life in a Noisy World.
Your attention can span only a very small number of things at the same time — we are talking in the range of 3–7 things at any given time. You don’t need to keep everything up at the same time. This is why you have memory and persistence on your devices to handle this for you!
Keep the number of tabs low, use a tab manager, or simply use the age-old concepts of bookmarks in your browser. Browsers like Safari even offer tab groups and similar concepts to bundle tabs in logical segments, so you get the best of both worlds.
This will keep your machine fresh and alive a lot longer, and much faster, and will spare your electricity bill too. Your mind (and computer) will thank you.
Hide the dock and keep it empty and clean by default
⏲️ ~2 minutes
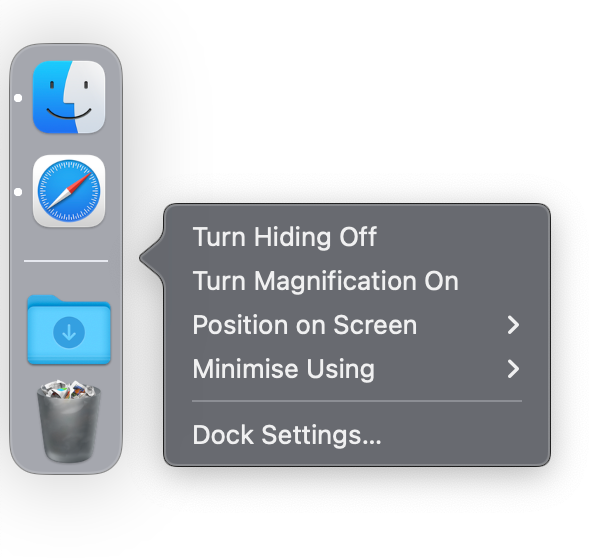
On Mac (and you can kind of do the same thing on Windows) I:
- Keep the Dock hidden, instead, I hover over Dock’s position to see it.
- Keep the Dock empty with as few apps running at a time as possible.
- Don’t store “recently opened” apps in the Dock, so it’s totally empty by default (except for the Downloads stack and trash bin).
- Minimize windows to the application icons.
- Remove any visual effects or cues.
This has been a way to keep me much more focused and grounded in what I want to achieve at any given time with far fewer distractions.
Restart your device
⏲️ ~2 minutes

It’s increasingly common for people to just keep their devices running indefinitely, but restarting (rebooting) is a time-honored way to get a bit of a clean slate and jettison some of the junk processes that have been accumulating over time. Combined with the other advice given here, you should get that — always too ephemeral — sensation of freshness again.
Do this at least every week. Remember the days when you did this several times per day? It’s not that hard.
Trash your third-rate socials
⏲️ ~30 minutes
Do you remember all the other social media? I mean before it was all just Tiktok (or whatever is in vogue right now)? Those quaint things people called Instagram, Facebook, Twitter, Myspace, Google+, or all of those niche communities like Discogs. Do a search—and this time I mean a proper Google search—to see what you find about yourself. Of all the sites you don’t want lingering around, old community sites and socials are the first to go. Just go ahead and delete those accounts.
Prune your remaining socials
⏲️ ~1 hour
I’m not at all a social media person, in fact, I only use LinkedIn precisely because it’s not a very social thing. But I take pruning the stuff on there, and on my website, pretty seriously. Make sure that whatever your media, message, and approach, it’s synced and something you want to have around:
- Check your photos: Incriminating party pictures from 2008 still there? Might want to nuke them.
- Check your posts: Wrote something you know was stupid (that you can’t stand for today) while you were drunk or depressed? Redact the record so those won’t come back and haunt you.
- Check your LinkedIn CV or other merits: Are they updated and any good? Take a pot of coffee and just get it in ship shape.
And so on.
I almost put this in the “Security” category since unmonitored, leaked, or resurrected socials can break people. Don’t get broken!
Prepare for your digital “death cleaning”
⏲️ ~5 minutes configuration + several hours/days for discussions and cleaning
Yikes, that came across as morbid, but hear me out.
“The Gentle Art of Swedish Death Cleaning,” a surprise international best seller, is actually a fond and wise little book. It’s about how to sort through and dispose of many of your possessions before you die, thus sparing your family members an unpleasant task.
“A loved one wishes to inherit nice things from you,” Magnusson writes. “Not all things from you.”
Charles Lamb, the English essayist, hoped his last breath would be inhaled through a pipe and exhaled in a pun. We…www.nytimes.com
Think of it. Let’s say I died here and now. I’d (currently) have quite some material possessions that would be unclear where they would go. Probably my family would have to decide what to do with it. There is no will written by me, for stuff like that. Then there’s money. That will follow national laws (because there is no written will) regarding its subdivision among my surviving family.
But, more crucially, what is to be done with the vastly bigger digital legacy I will leave behind?
Some of these digital assets are static — like files — and others are living or social — like some of my online accounts and places of presence. That’s where tools like Apple’s (and Facebook’s) Legacy Contacts and Google’s Inactive Account Manager come in. You will of course have to have conversations with whoever will be your legacy contact, which will probably take more time than flipping the switch.
This activity also entails ensuring you clean up any digital storage — hard drives, physical media, your computer(s) and device(s), and cloud storage — which has the benefit of being of immediate use to you as well. If you want concrete step-by-step instructions look no further than The Verge’s article on this matter.
Summary of key points
Security
- Turn on automatic updates.
- Set up backups.
- Check if your credentials have been leaked.
- Use unique passwords and don’t reuse any passwords across sites or apps.
- Use strong passwords everywhere.
- Use MFA or passkeys.
- Vet all browser extensions and eliminate as many as you can.
- Remove unneeded third-party connections.
Integrity
- Remove unused accounts.
- Get a browser that isn’t Chrome.
- Add Cloudflare 1.1.1.1 or something similar.
- Use a good, paid email service.
Cleanliness
- Remove or tone down all notifications.
- Clean your computer physically.
- Remove files, apps, and processes hogging your device.
- Use bookmarks, close tabs.
- Get into zen mode with a hiding, minimalist Dock.
- Restart your device every now and then.
- Trash socials you are not actively using.
- Prune your remaining socials.
- Go through all of your digital estate and make sure someone can access your things if you die or become incapacitated.
Step by step to a more zen online/computer life
Keep in mind that doing any of the above won’t transform the world into an enchanted Disneyland in a jiffy, but it will make sure the bad people have a hell of a lot more work to do to harm you, and that you have a device that’s set up for you to do your best work. The majority of activities aren’t too hard either, as you saw.
That’s all, folks. Hope you take the time to make some of these changes—it will be worth it!